Solution - Week 0x01
The challenge can be found here
Solution
After reading the description, we can say that we will have to use some forensics, cryptic, and steganograpgy tools to solve this challenge.
Firstly, we can see the zipped resource, so we will just unzip it.
root@host# unzip challenge-week-1-main.zipArchive: challenge-week-1-main.zip4658b1d2bcbeb15a25b5fc5fa04953a80914e4a9 creating: challenge-week-1-main/ inflating: challenge-week-1-main/README.md inflating: challenge-week-1-main/resources.zip
root@host# cd challenge-week-1-mainOnce we cd into the challenge-week-1-main directory, we find a README.md and resources.zip. The README.md contains the same description that we can read on the url provided above.
Upon unzipping the resources.zip in the similar manner we did with challenge-week-1-main, we will just go into the resources directory.
root@host# cd resourcesWe encounter a secret.png and if we try to open it, we face some issues (just as described in the description).
Even if we try to open the jpg with multiple commands like eog or mpv or xdg-open or if we just double click on the image, we fail to open it.
This means that the file is corrupted or maybe this isn’t an image at all. To check that, we will use the file command with this jpg.
root@host# file secret.pngsecret.png: Zip archive data, at least v2.0 to extract, compression method=deflateWe can see that this wasn’t an image indeed. This is a zip archive, so let’s rename it as .zip and try to unzip it.
root@host# mv secret.png secret.zipsecret.pngsecret.zip
root@host# unzip secret.zipArchive: secret.zip inflating: vault/null.txt inflating: vault/secret.txtLet’s head inside this vault folder to see what’s up.
root@host# cd vault
root@host# ls
null.txt secret.txtwe find that there are two txt files. upon further inspection, we can see that null.txt seems to be empty but with something suspicious going on. Although it is empty, it still has some lines of storage.
the secret.txt file is having some data in a single line that looks like a hex-code. To check our claims let’s head to cyberchef. We can either open our secret.txt as input or we can just copy paste its contents into the input.
We will use the From Hex operation on our input. Well will find the output to be as follows
ÿØÿà JFIF ÿÛ C
% #
, #&')*) -0-(0%()(ÿÛ C
(((((((((((((((((((((((((((((((((((((((((((((((((((ÿÀ " ÿÄ
ÿÄ µ } !1AQa "q2¡#B±ÁRÑð$3br%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
¢£¤¥¦§¨©ª²³´µ¶·¸¹ºÂÃÄÅÆÇÈÉÊÒÓÔÕÖ×ØÙÚáâãäåæçèéêñòóôõö÷øùúÿÄ
ÿÄ µ w !1AQ aq"2B¡±Á #3RðbrÑ$4á%ñ&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
¢£¤¥¦§¨©ª²³´µ¶·¸¹ºÂÃÄÅÆÇÈÉÊÒÓÔÕÖ×ØÙÚâãäåæçèéêòóôõö÷øùúÿÚ
? ðøã =±R¬%Häãò©#kð¢¥UÜÄ®Ü c^3ÜöêFªA äuÍJ©¼£ ©ãj P~"&cØ<snip>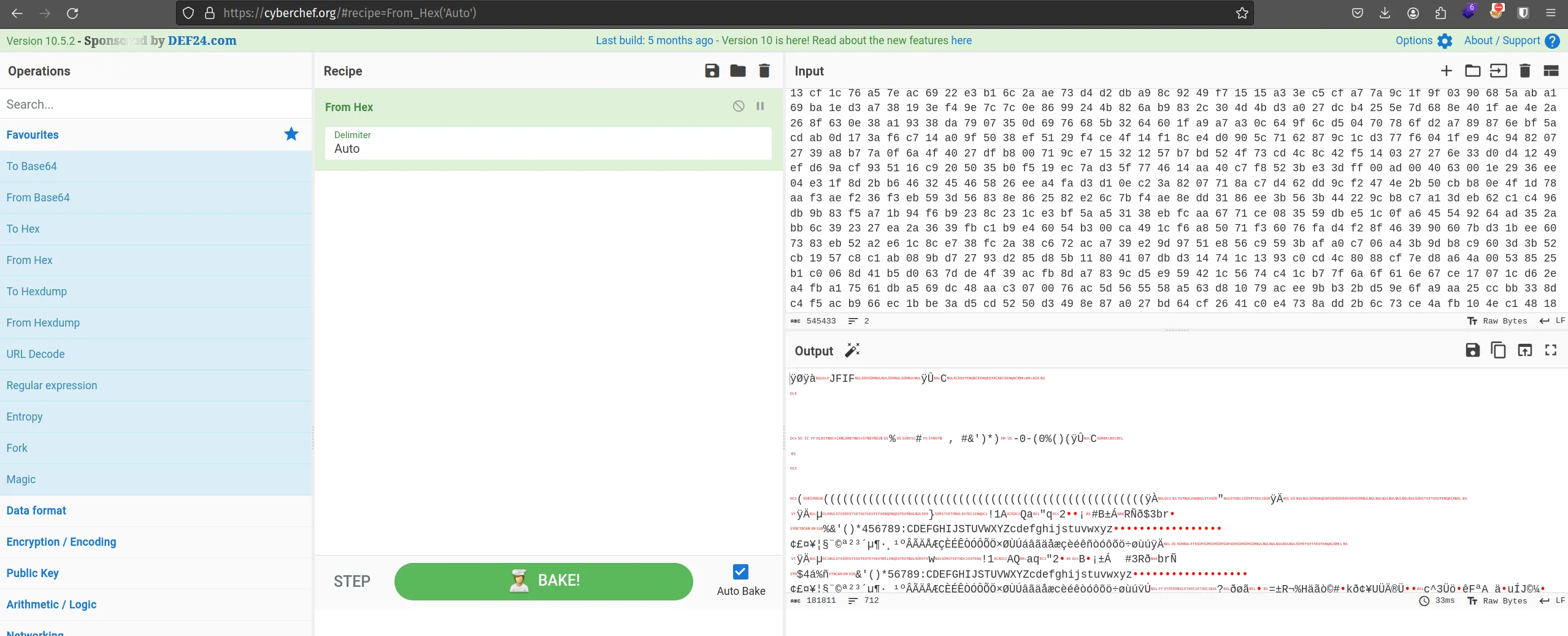
Well the JFIF in the starting indicates that this is the data of a jpg file. So we wil just save this image via Save output to file option. I will save it as download.jpg.
If we open this file, we see the image of a cat. This might be a hint to using the cat command somewhere, but I will let you huys explore that on yourself.
Now going back to the null.txt, I first simply searched ctf empty character character file on google, which gave me these results. I went on the understant this ZWSP blog but it didnt seem to help.
I tried the python technique to see the hex-characters in the file by opening the interactive mode of python or IDLE and just pasting the entire content of null.txt as a multiline string with three quotes.
root@host# pythonPython 3.11.6 (main, Nov 14 2023, 09:36:21) [GCC 13.2.1 20230801] on linuxType "help", "copyright", "credits" or "license" for more information.>>> '''............................................................................................................................................. '''' \t \t \n\t\n \t\t \t\n\t\n \t\t\t \t\t\n\t\n \t\t\t \t\t\n\t\n \t \n\t\n \t\t \t \t\n\t\n \t\t\t \t\t\n\t\n \t \n\t\n \t \t \n\t\n \t \t \n\t\n \t\t \t\n\t\n \t\t \t\t\n\t\n \t\t \t \t\t\n\t\n \t \t \t \n\t\n \t\t \t\t\t\t\n\t\n \t \t \n\t\n \t\t\t \t \n\t\n \t\t \t\t\t\t\n\t\n \t\t\t \t \n\t\n \t\t \t \t\n\t\n \t\t \t\t\n\t\n \t\t\t \t \n\t\n \t \t \n\t\n \n'>>>But it is clear that there is no scope for ZWSP here as there are only empty-spaces, tabs and newlines here. Upon further research, I came to know about Whitespace Language Encryption
So to decrypt this cryptic language, I went to decode.fr and they had a solution for me here
Using the options provided on the decode.fr page, we could wither select the null.txt file or paste it contents as input. We will get the output as
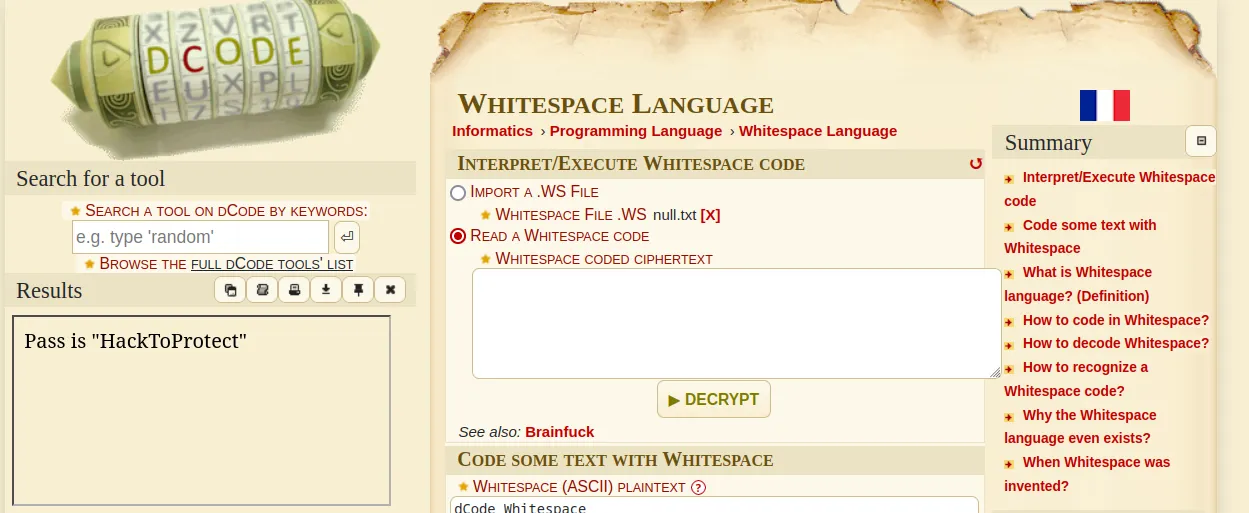
Pass is "HackToProtect"I wonder where this password can be used?…
If we remeber, there was mention of steganography and steghide is a tool that uses steganography with JPGs using password (I know it from experience). So we will try to extract data from the download.jpg that we got from secret.txt.
root@host# steghide extract -sf download.jpg -xf output_file.txt -p HackToProtect
wrote extracted data to "output_file.txt".You can ask about the flags and syntax of steghide to extract a file from ChatGPT, it is pretty accurate. We can see that last line says wrote extracted data to “output_file.txt”. which means output file hash been created. Let’s see what is inside it.
root@bash# cat output_file.txtFile: output_file.txt4d 5a 57 47 43 5a 33 33 49 4d 32 48 49 34 32 37 47 52 5a 44 47 58 5a 55 4e 52 33 54 49 36 4c 54 4c 35 52 58 4b 3542 54 48 35 36 51 3d 3d 3d 3dThis seems like hex-code again. Let’s go back to CyberChef for this. We recieve the output as…
MZWGCZ33IM2HI427GRZDGXZUNR3TI6LTL5RXK5BTH56Q====This seems like Base32. Lets use the From Base32 operator in cyberchef to decode this. We recieve:
flag{C4ts_4r3_4lw4ys_cut3?}This seems like a flag to me. Let’s try submitting it to the discord channel.
/submit-flag flag{C4ts_4r3_4lw4ys_cut3?}And this gets accepted!!!